Nothing generates more stress and fear than looking for our smartphone and not finding it. If the worst has happened, we show you in this article how to locate my mobile if it is stolen.
Keep in mind that there are various methods, this regardless of whether we are talking about a mobile with Android or iOS operating system. Here we will show you the most popular ones or even how to delete your data in case there is no way to recover it.
Methods to locate your smartphone in case of theft or loss

Despite the fact that there are a large number of free or paid tools to locate a lost mobile, operating systems have their own functions. Here we will show you how to search for your equipment easily and simply.
These searches can be done from other computers or from your own as a test, so you will better understand the process to be executed. Without further ado, we will tell you how to locate my mobile if it is stolen.
How to locate my Android mobile if it was stolen
As we mentioned before, there are a large number of applications that can help you, but this time we will focus on the Google tool. The application called “Find my device”, is located in the official Google Play store.
Does not require complex configurations, its operation is based on the original configuration of the device, where email is the base. The application only proceeds with the connection of the data generated by the mobile in terms of position and shows us where it is.
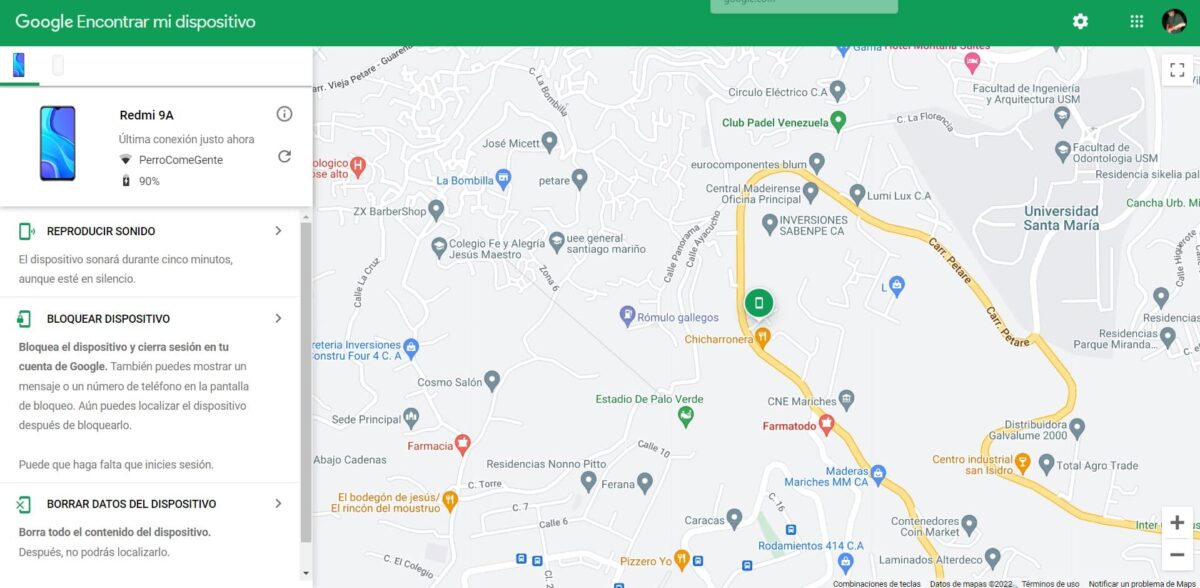
Possibly at this point you are wondering, what is the use of this tool in case of loss. Well, the advantage is that you can connect from any other device, including your computer. To view it you must enter the site of Google Find my device and it will show a map with the location.
Between the data that will offer you in real time you can find when your last connection was, to what network, the name of the equipment or even the percentage of battery you have.
As if that were not enough, you also have a series of functions in case someone unauthorized has taken your equipment. These are:
- device lock: This will allow you to lock the device and log out of Google, showing a message on the lock screen. Despite this, you can still locate yourself.
- play sounds: Even if it is silent, the equipment will make loud sounds for 5 minutes. This will allow you to find him if he is nearby.
- Clear your mobile data: This is an extreme method, which is designed when we consider that we will no longer be able to locate the equipment. Delete everything on your computer and you will no longer be able to locate it.

How to locate my iOS mobile if it was stolen
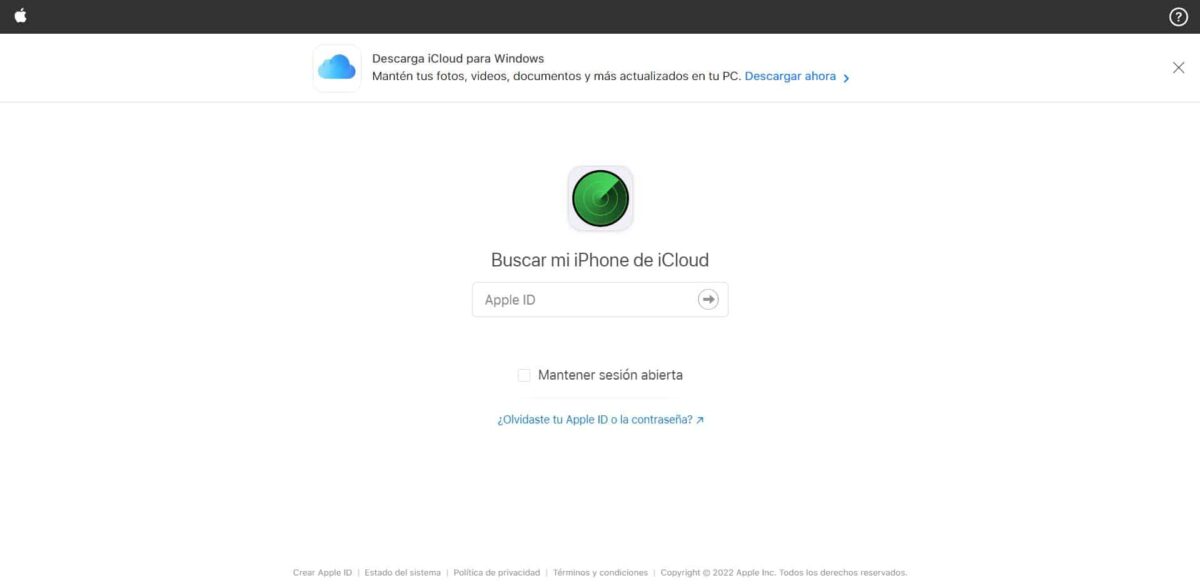
As with Android, iOS has taken the security and safeguarding of personal data very seriously. In this case, there is an interesting tool to locate the mobile, it is called "Search my Iphone".
As in the previous case, this does not require a particular configuration, the data generated by the mobile will give us the necessary tools. If you want to know the location from another device, you only need the credentials that you commonly use on the device to be located.
In the same way as in Android, you can also use your computer, if you are from a Mac computer, you will have the "Search" application, integrated into the operating system itself. If you want to access from a PC, you can do it through the web browser on the site of iCloud.
Through iCloud you can:
- Locate the device on a map: which will give you an idea of exactly where it is and be sure if it is lost or someone unauthorized took it.
- play sounds: emits a sound that will let you know if it is in the same place as you.
- Lock the computer: to do this you must mark the device as lost, which will show a personalized message on the device screen and prevent access.
- Clear the content: This will keep the content of your device safe, deleting everything that exists on it, but the lock will remain active and will not allow access to it.
A very remarkable element in this method of location and recovery of our mobile is that can be located off. This as long as it is relatively close, since it uses Bluetooth connectivity. Maybe this isn't really very useful at a distance, but up close, it sure is.
Cases where it is not possible to locate your lost mobile device

There are cases where the location systems for your mobile will not work, which will prevent the use of applications. These cases are:
- The computer is not turned on: it is mandatory that the equipment is turned on, otherwise it will not emit signals nor will it be able to connect to networks with internet access. Only iOS devices can work this way and at a very short distance.
- Session not started: It is important to remember that many applications require data generated by Google to give location, if the session is closed, you will not be able to locate it.
- Without an internet connection: Regardless of whether this is done through mobile data or a WiFi network, connectivity is essential to acquire the position or even take actions such as blocking or deleting files.
- location off: Remember that privacy on these devices is an element to highlight, so location can be turned off. In case this happens, applications will not be able to set the position.
What to do if I can't get it back

In case you are sure that you will not be able to access your mobile and confirm that it is stolen, it is recommended that you initially remotely delete all the content that it has, remember how valuable personal information is to friends of others.
Another recommendation is report your mobile line as lost or stolen to the company that provides the service. This will avoid the possibility of fraud in your name or even unnecessary expenses to your telephone bill.
Finally, remember to report to the authorities that you were the victim of a robbery, because in addition to serving as statistics, it will alert law enforcement officials and prevent this from happening.